Threat Hunting - Simplifying The Beacon Analysis Process - Active
In part one of this two-part series, I described what is involved with performing a beacon analysis and why it is so important […]
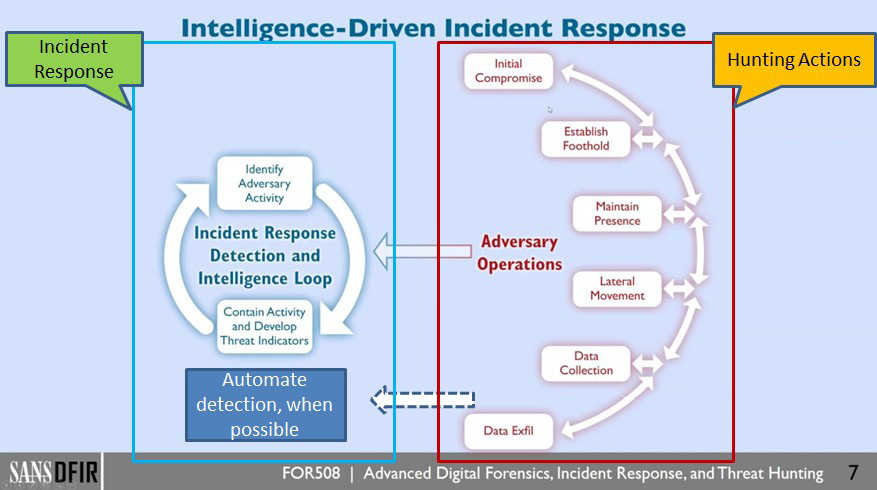
Offensive Intrusion Analysis: Uncovering Insiders with Threat Hunting and Active Defense – CSIAC

Detecting Beaconing Attacks by Advanced Threat Hunting
Even More on Threat Hunting

Stamus-Networks-Blog

New sophisticated email-based attack from NOBELIUM

Threat Simulator - Active Countermeasures

Threat Hunting Beacon Analysis
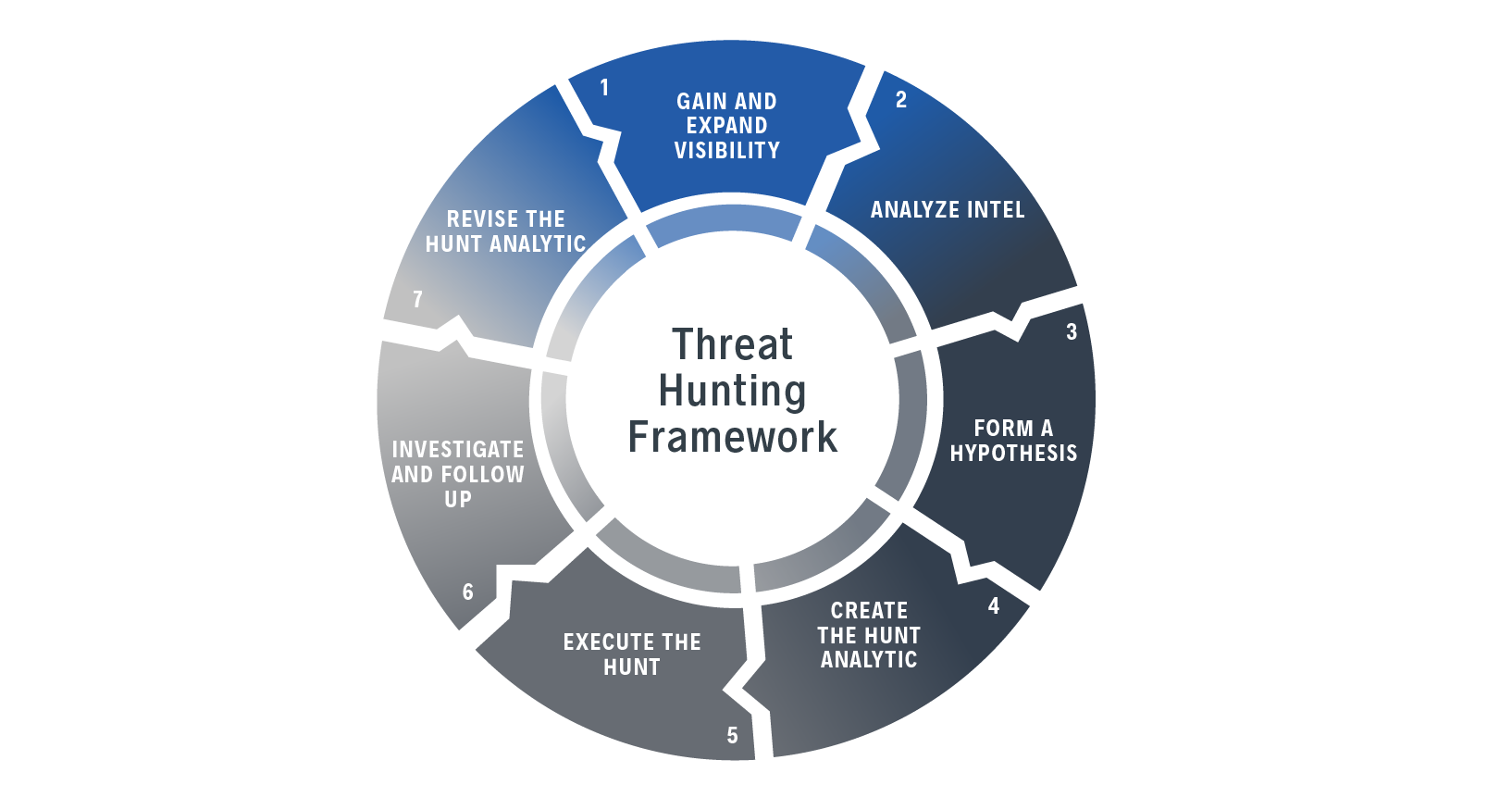
How Threat Hunting Can Evolve Your Detection Capabilities - Gigamon Blog

My Saturday with Active Countermeasures

Threat hunting: Part 1—Why your SOC needs a proactive hunting team
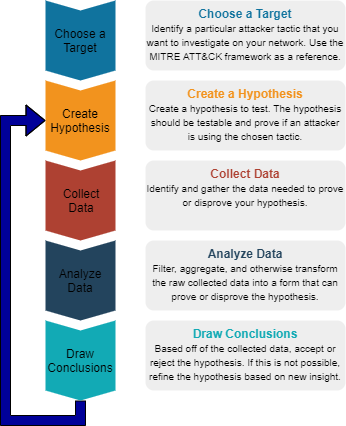
Threat Hunting. Basic Concepts

Threat Simulator - Active Countermeasures
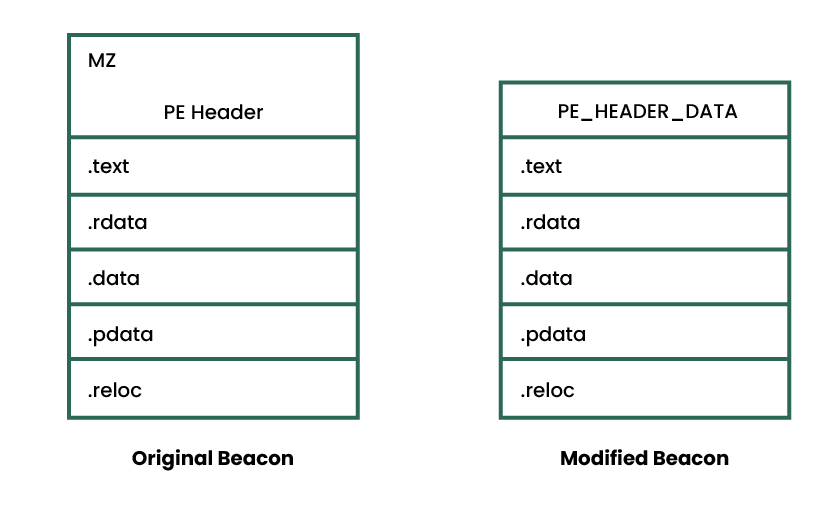
Revisiting the User-Defined Reflective Loader Part 2: Obfuscation and Masking
.png?width=2000&height=800&name=Hunt%20information%20informs%20rule%20variables%20and%20level%20of%20specificity%20(1).png)
Building a better detection ecosystem

Picus Labs Threat Newsletter - September





