Four types of fake key attacks. Each diagram represents Alice
Download scientific diagram | Four types of fake key attacks. Each diagram represents Alice (left), her contacts (right), and an adversary (center). The green lines represent secure connections; the red lines represent compromised connections. Note that in each situation, there may be other pairs of clients communicating securely that are not shown. from publication: Automatic Detection of Fake Key Attacks in Secure Messaging | Popular instant messaging applications such as WhatsApp and Signal provide end-to-end encryption for billions of users. They rely on a centralized, application-specific server to distribute public keys and relay encrypted messages between the users. Therefore, they prevent | Automatism, Security and Server | ResearchGate, the professional network for scientists.
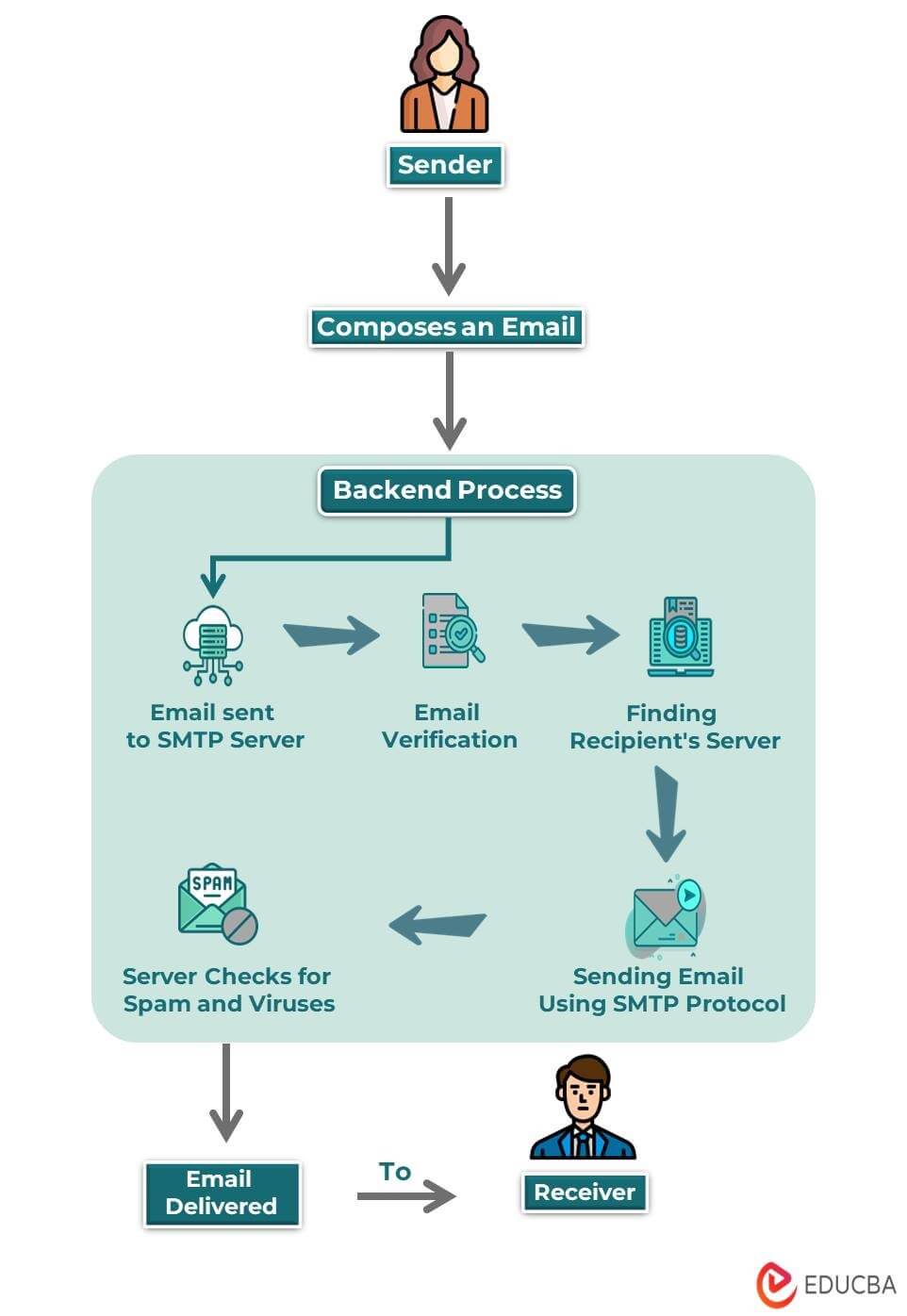
What is Email? Components, How it Works, Types, Templates
Forgery attack on optical encryption based on computational ghost imaging

What is 256-bit Encryption? How long would it take to crack?

The proposed operational context diagram.

Throughput comparison between OrgAn and PriFi systems for

Daniel Zappala's research works Brigham Young University - Provo
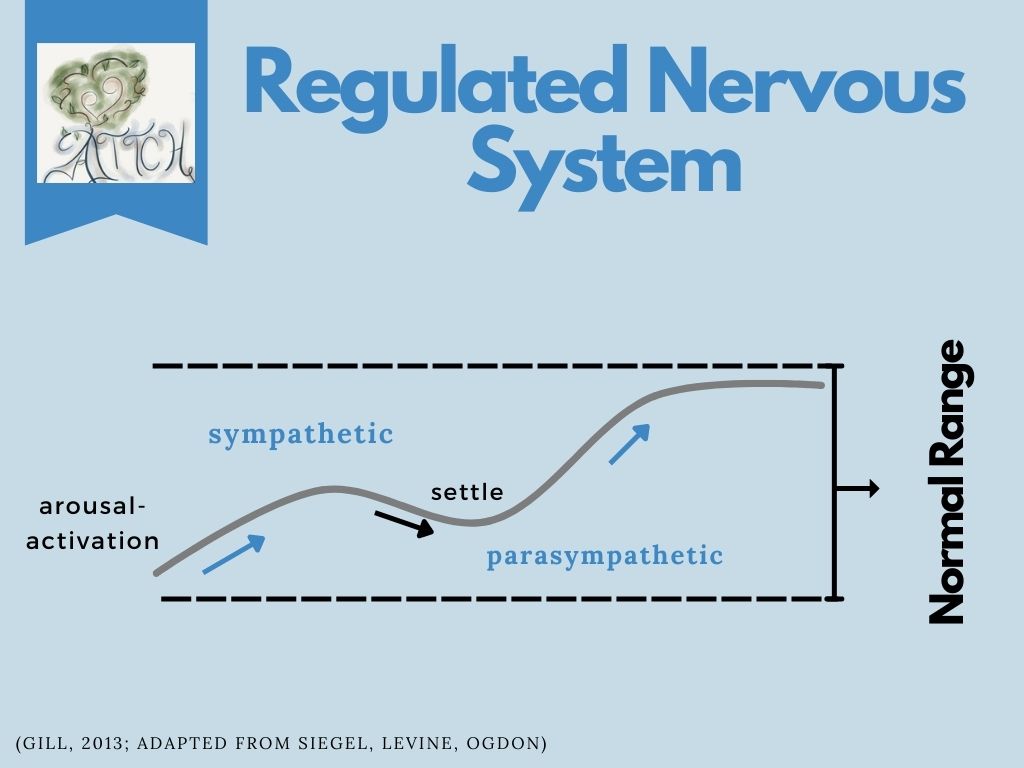
Understanding and Working with the Window of Tolerance - ATTACHMENT AND TRAUMA TREATMENT CENTRE FOR HEALING (ATTCH)

Amir HERZBERG, Professor, Professor

Devashish GOSAIN, Postdoc, PhD
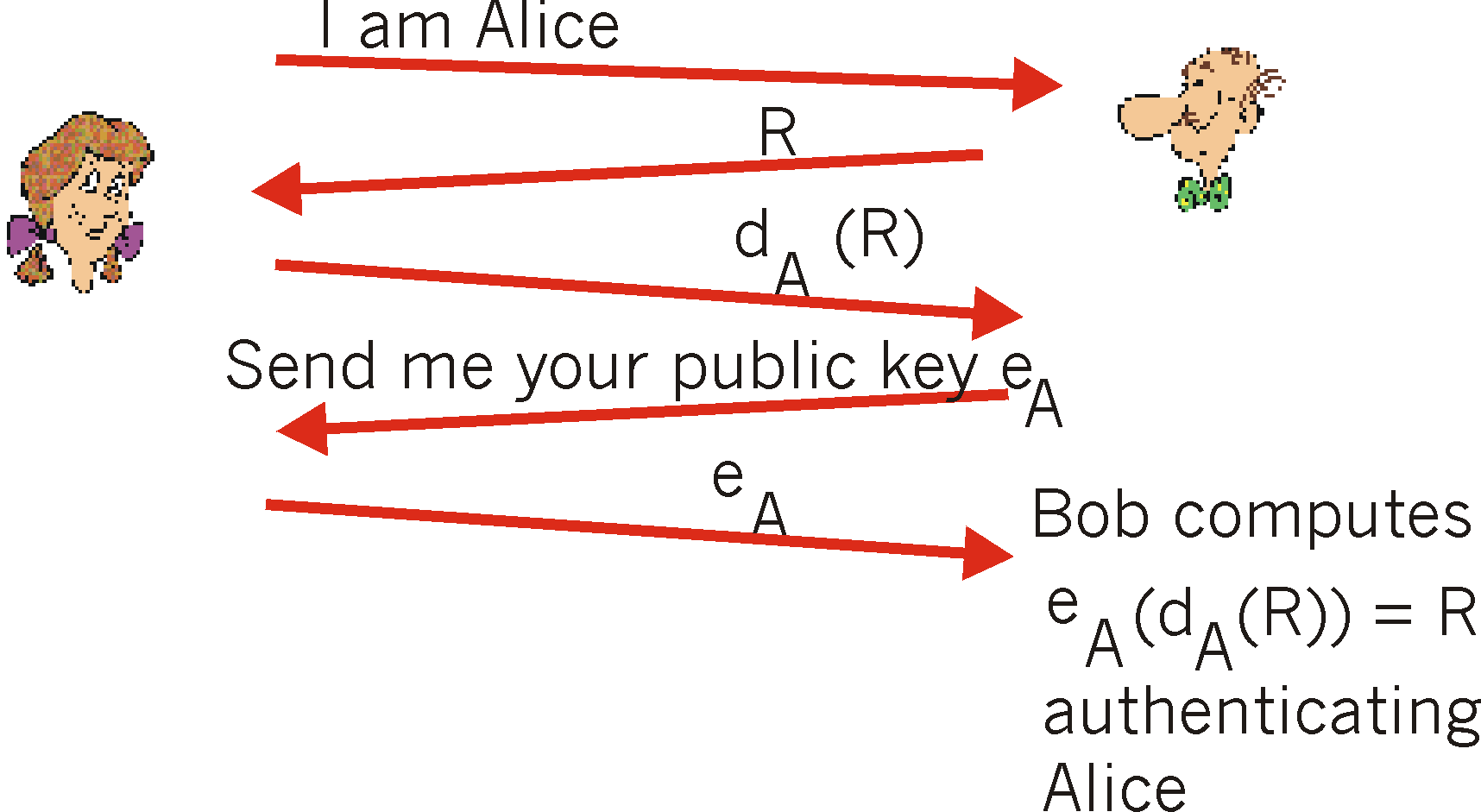
Authentication









